Secure Access Service Edge (SASE): Converging the Latest Security and Networking Technologies to Enable Secure and Fast Cloud Transformations
When it comes to creating business value through digital transformation, speed is essential. In cases where speed to market matters, the networking infrastructure that the organization selects requires flexibility, agility, elasticity, and security enabled by automation.
That’s because the explosion of cloud computing, IoT, mobile, and remote user requirements has also altered how we view networking and security. To take on these challenges, a traditional architecture—one that treats networking and security separately and is implemented using multiple point solutions managed as silos—is no longer an effective strategy.
Ask the Experts: An Interactive SASE Panel with Burwood and Cisco
As you continue your digital transformation journey focusing on secure access to data and applications across the cloud, take a moment to learn more about SD-WAN and SASE.
View on Demand →The answer: Secure Access Service Edge (SASE)
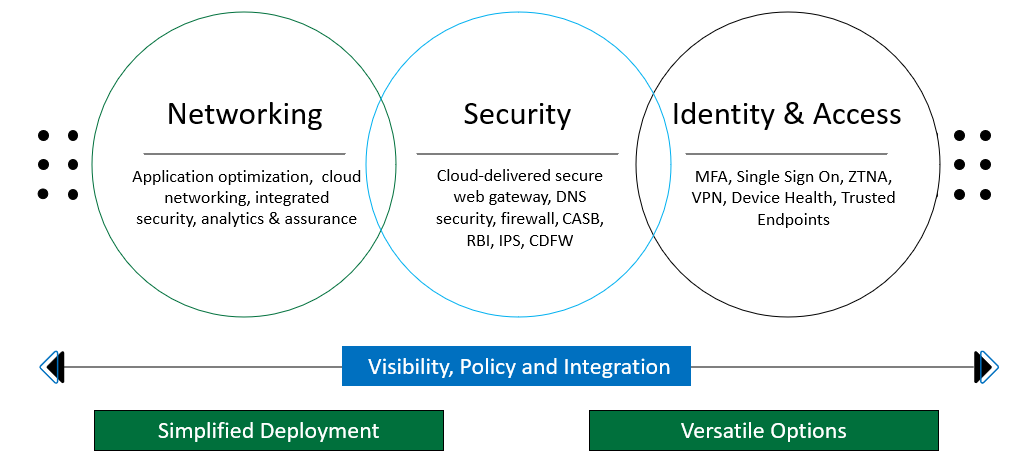
This cloud-based security architecture framework was coined by Gartner analysts Joe Skorupa (networking) and Neil McDonald (security) in 2019. SASE converges the best security and network connectivity technologies into a single platform to enable secure and fast cloud transformations.
Since the inception of SASE, there remains a constant buzz around the technologies and their combined capabilities. 92% of IT organizations have already started their cloud migration journey, and 60% of enterprises plan to adopt SASE-based services until 2025.
SASE builds on existing technologies such as SD-WAN and cloud access security brokers (CASBs) by combining software-defined networking with network security functions delivered as a service through the cloud. SASE also promises a more flexible architecture with built-in security that helps deliver positive end-user experiences—by generating a set of capabilities that address technological and business needs with the scale and flexibility to meet digital transformation objectives.
Secure Access Service Edge (SASE) Adoption Transformation Drivers
Even with the hype surrounding SASE generated by Gartner and many networking and security companies, it’s essential to recognize that SASE is more than just a buzzword. As the following research notes suggest, today’s business requirements—for remote/hybrid employees, -sophisticated security threats, and hybrid clouds—have driven the need to view network and security solutions from a broader perspective:
A recent Gartner survey revealed that 82% of company leaders plan to allow employees to work remotely some of the time. In contrast, another Gartner survey revealed that 74% of CIOs plan to permanently shift employees to remote work after the pandemic ends.
In addition to social engineering and ransomware attacks being on the rise, multi-vector DDoS attacks targeting network layers 3, 4, and 7 have risen 42% since 2020.
A recent IDG survey revealed that 94% of organizations believe their online security had improved after switching to cloud computing. Moreover, a recent Salesforce survey found that 80% of businesses believe that cloud computing adoption delivered operation improvements within the first few months. In addition, ESG discovered that the number of organizations committed to or interested in a hybrid cloud strategy has increased from 81% to 93% since 2017.
The Benefits of Secure Access Service Edge (SASE)
By deploying a SASE framework, organizations benefit from several key capabilities:
Advanced reliability, scalability, and compliance
Improved functional agility, efficiency, and visibility
Greater operational agility, performance, and scalability
Enhanced collaboration, efficiency, and cost optimization
Faster time-to-market and incident handling
Increased application performance
Greater bandwidth and lower latency to support remote users
Flexibility to adopt the latest technologies like IoT and artificial intelligence
In the security realm, organizations gain the flexibility to implement a wide range of preventative policies to stop threats and prevent data loss—including web filtering, sandboxing, DNS, credentials, and next-generation firewalls. SASE also reduces risks by addressing unique challenges among distributed users and applications. With security as a core component of the connectivity model, SASE ensures all connections are secure and encrypted, regardless of location or application.
Transitioning to Transformation with SASE
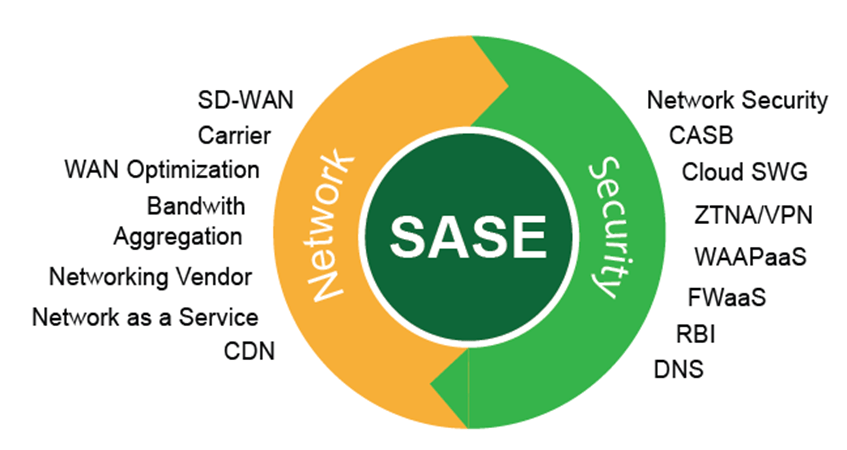
Pulling all of these components together produces the secure, scalable results organizations are looking for with digital transformations to the cloud. The main components of SASE include
SD-WAN controls connectivity, management, and services among data centers, remote branches, and cloud instances. SD-WAN provides a software-defined approach to managing your wide area network (WAN), enabling transport independence to securely connect users to multiple network locations.
DNS Layer Security protects your end-users from sites hosting harmful content by blocking connections to malicious or unwanted domains. Enforcing security at the Domain Name System (DNS) and IP layers is the first line of defense against threats.
Secure Web Gateways (SWGs) are cloud-based web proxies that provide security functions such as malware detection, file sandboxing and dynamic threat intelligence, Secure Socket Layer (SSL) decryption, app and content filtering, and data loss prevention (DLP). SWGs are essential for filtering malicious or otherwise unwanted traffic.
Firewall-as-a-Service (FWaaS) applies a cloud-based set of rules and filtering to prevent non-web Internet traffic . This typically includes Layer 3 and Layer 4 (IP, port, and protocol) visibility and control, along with Layer 7 (application control) rules, and IP anonymization.
Cloud Access Security Brokers (CASBs) help to control and secure the use of cloud-based applications by monitoring all application activity. A CASB enforces security policies and compliance regulations between cloud service consumers and providers.
Zero Trust Network Access (ZTNA) verifies user identities and establishes device trust before granting access to unauthorized applications, data, and services. ZTNA helps organizations prevent unauthorized access, contain breaches, and limit an attacker’s movement on the network.
Centralized Management from a single console streamlines change control, patch management, outage window coordination, and policy management.
With all these capabilities, the result is all-encompassing. But from an architecture, implementation, and management perspective, it is possible to implement SASE through a phased approach. There can be many paths to transformation—some organizations start with network upgrades while others begin with security upgrades.
Explore SASE With This Practical Workshop:
Our cloud experts help you identify priority use cases, evaluate current workstreams and policies, and build a lightweight roadmap to success.
Turn to Burwood to Enable Your SASE Transformation Strategy
To implement SASE in a practical, cost-effective, phased approach that makes sense for your organization, Burwood is here to help. We meet you where you are on your journey and help you transition seamlessly and securely to SASE. By working with us, you can identify your most important use cases and build a roadmap to achieve your goals:
Create a long-term remote access plan for users.
Develop a converged network and security solution.
Secure your SD-WAN infrastructure.
Streamline public and private application connectivity across branch locations.
Enable centralized management, policy-based security, and visibility.
Defend against threats across on-premises and cloud environments.
Learn more about SASE and how Burwood can help you with your SASE strategy: https://www.burwood.com/sase
Burwood’s SASE Visioning Workshop helps you create a secure cloud networking infrastructure roadmap based on your key requirements and user needs. Learn more and sign up here: https://www.burwood.com/sase-workshop