Ransomware Protection
Attacks on corporate data and systems are growing exponentially. No organization is safe from being targeted, regardless of size or location. Does your corporate security posture include tools and processes to safeguard against the inevitable attack? A ransomware protection plan is an essential component of your enterprise security posture and strategy.
Ransomware Protection Self-Assessment
The world saw an alarming 105% surge in ransomware attacks in the last year alone.
How protected is your business from ransomware cyber threats? Take this short assessment to find out.
What Is Ransomware?
Ransomware is a type of malware threat attackers use to infect systems and encrypt files. The attacker then demands a payment from the victim, typically with a promise to restore the files or access upon payment receipt.
Types of Ransomware
There are two types of ransomware you’ll encounter in attacker events:
U.S. Government Ransomware Recommendations
In June 2021, the White House issued a memo warning corporations to take immediate steps to protect their corporations from ransomware attack. Today's cybercriminals are not just stealing data; they are trying to take down your most critical systems and operations. The White House memo recommends these best practices to safeguard against attacks:
- Backup your data, system images, and configurations, regularly test them, and keep the backups offline
- Update and patch systems promptly
- Test your incident response plan
- Check your security team’s work
- Segment your networks
Crypto Ransomware: A type of harmful program that encrypts files stored on a computer or mobile device in order to extort money. It essentially takes the files hostage, demanding a ransom in exchange for the decryption key needed to restore the files.
Locker Ransomware: Attacks lock down the entire computer instead of encrypting specific files. Attackers then promise to unlock the device if the victim pays the ransom. A locker attack typically allows the user to boot up the device.
Common Access Tactics
Ransomware attackers use a variety of creative tactics to gain access to the victim’s data or systems. Some of the most common include:
Phishing: The attacker sends the malicious files to the victim as an email attachment, masking the content to appear as a person or file that the victim can trust.
Social Engineering: Gaining access to a victim’s systems or data via human contact and psychology, instead of technical hacking tactics. For example, convincing a victim to reveal their password by impersonating an IT support person.
Drive-by-Downloads: Unintentional malicious file download authorized by the victim, such as malware masquerading as a security update.
Username and Password Compromise: Publication of the victim’s username and password data, thereby enabling attackers to use the login to infiltrate systems.
Creating A Ransomware Protection Plan
Defending your data and systems from this wide variety of attack methods can seem complex. There are hundreds of manufacturer point solutions available in the market, providing tools and systems for things like:
Email Security
Web Security
Rights Management (PAM)
Access Management (IAM)
Endpoint Security (EDR)
Vulnerability Management
Incident Response Plan
How do you decide which areas and tools to prioritize? Start with creating a ransomware protection plan to guide your staffing, tooling, and investment decisions. Burwood Group recommends focusing of four key areas to ensure you prioritize the essential components and minimize distraction from your goals:
1. Develop Your Incident Response Process and Procedures
Shifting your mindset from “avoiding a ransomware event” to “proactive detection and response” requires development, planning and testing of a holistic incident response process. Working from an assumption that a ransomware event will occur, you should develop plans to respond and recover critical business operations and restore a secure environment. This plan should include:
Roles and responsibilities assignment,
Identification of critical business applications,
Evaluation of recovery timeframe and data recovery objectives, and
Documentation of recovery runbooks.
Once this process has been developed, executing a “tabletop exercise” to simulate a ransomware event helps to surfaces gaps in the plan and identify areas for refinement.
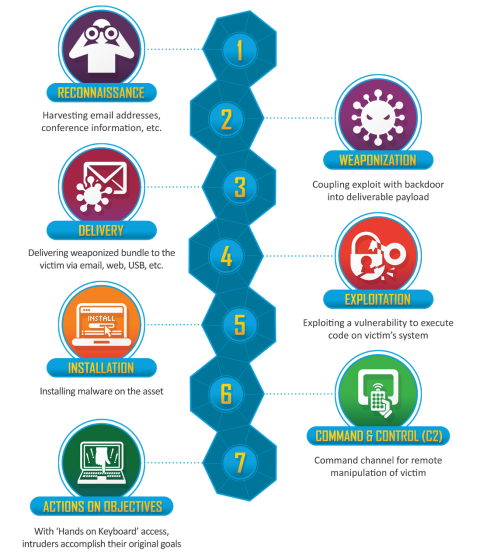
The cyber kill chain framework is a model for identification and prevention of cyber attacks.
2. Implement Risk Reduction Controls
We recommend leveraging the cyber kill chain framework for planning and defending against ransomware. Breaking the chain of attack actions can block a ransomware event from fully executing and can reduce the lateral movement potential for an attacker. We focus on the core activities that a malicious user will exploit in an organization.
3. Validate Your Data Backup and Recovery Solutions
Even with the best ransomware defensives, it is possible that your organization will experience a loss of data due to ransomware. Planning for data backup, recovery and validation is key to ensuring that you can avoid expensive ransom payments and returning to business operations as soon as possible.
4. Create a Vulnerability Management Plan
Attackers will attempt to exploit the “lowest-hanging fruit” vulnerabilities in your environment to gain an initial foothold. From there, they expand. Implementing continuous vulnerability management gives your organization visibility to reduce the risks. Missing patches and misconfiguration of “default” settings are the most common attack vectors for hackers and enabling your security operations team to find and address these vulnerabilities is critical to reducing the attack surface and encouraging hackers to “move along”.
Getting Started
Burwood Group helps enterprise IT leaders create security systems and toolsets that prevent ransomware attack. Engage our team to help you with:
Ransomware Protection Self-Assessment
The world saw an alarming 105% surge in ransomware attacks in the last year alone.
How protected is your business from ransomware cyber threats? Take this short assessment to find out.
Security Tools Gap Analysis
When is the last time you reviewed the purpose and performance of your enterprise security tools? Engage Burwood to complete a tools gap analysis.
- Document current tooling infrastructure and performance
- Provide insight on vendor rankings and roadmaps
- Present recommendations for consolidation, replacement, upgrades, and cost-savings
- Check your security team’s work
Ransomware Plan Development
Creating a ransomware plan is a strategic, critical project. Engaging a third party like Burwood to lead the process helps keep your staff focused an productive.
- Evaluate your current-state processes and tools
- Define critical workstreams and lead associated workshops, documentation, and approvals
- Execute tabletop exercises to test plan success